Empire tool is one of the post-exploitation frameworks with an HTTP module; attackers can use it for various malicious purposes, for example, C&C.
Empire HTTP traffic analysis
Using the Empire and its HTTP module: After the attacker infiltrates the victim system and communicates with the C&C server, the connection on the HTTP protocol provides the following evidence:
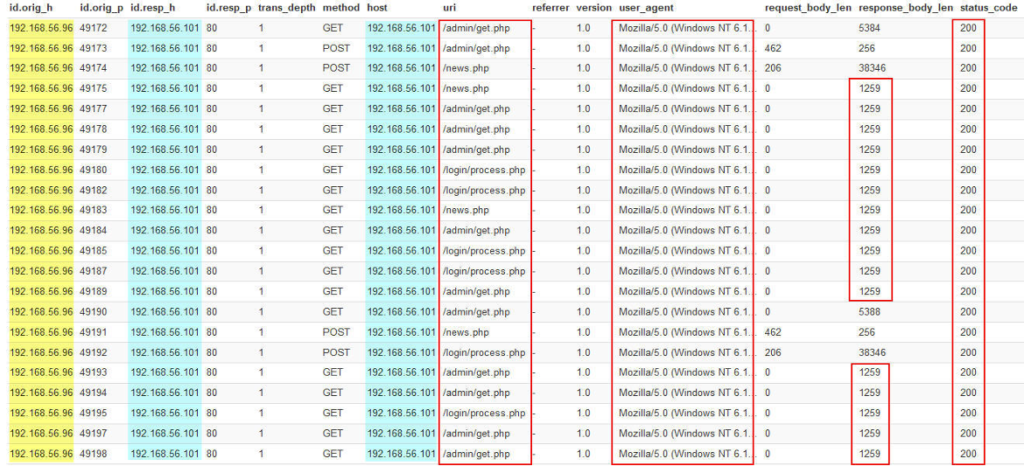
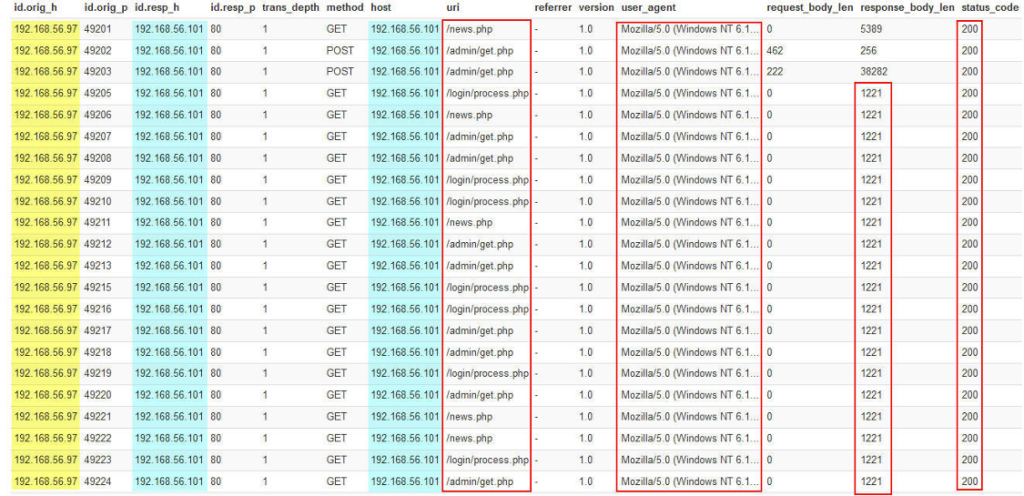
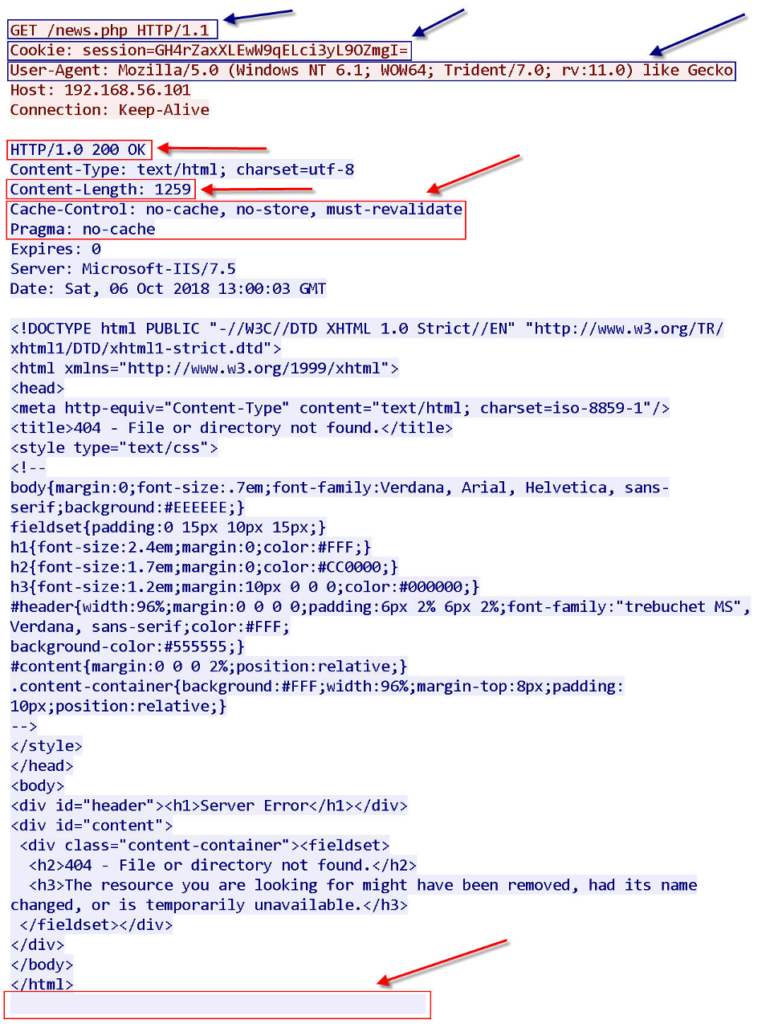
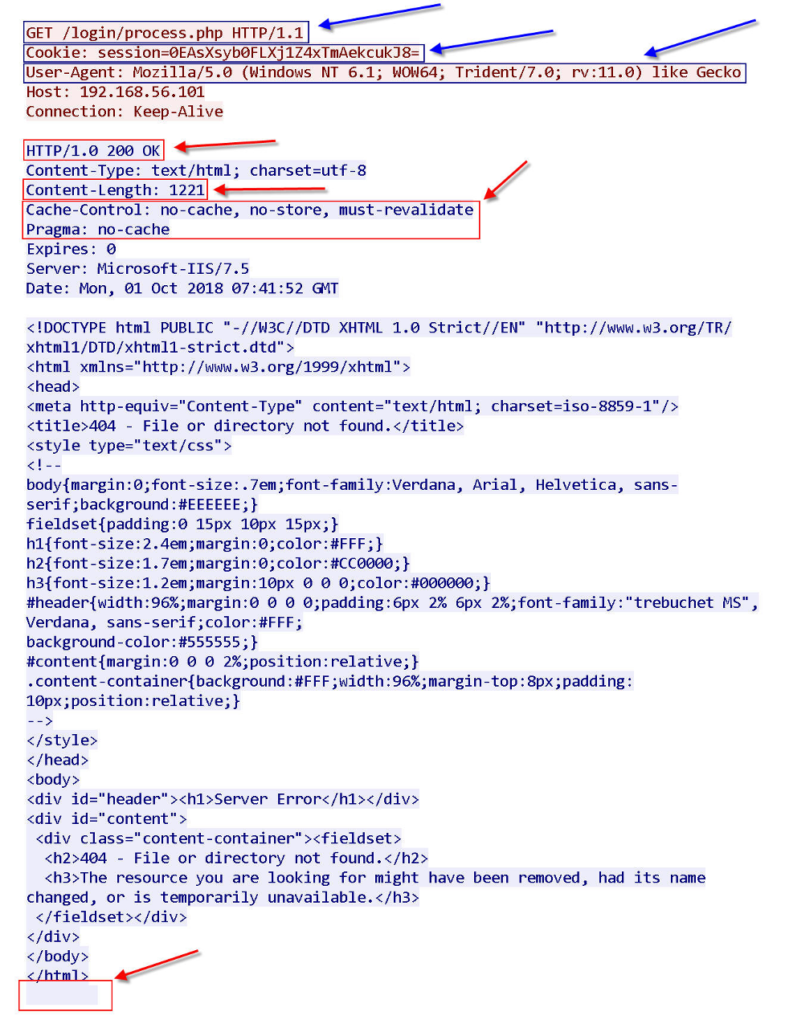
Explain the sections highlighted in the figures above:
HTTP Request analysis :
GET:
As you know, one of the HTTP methods is that it sends HTTP requests to the /news.php, /admin/get.php, and /login/process.php pages.
The first characteristic to detect this tool is these .php pages but this URL is easily editable by a novice intruder.
Tip: HTTP request client sent with HTTP 1.1 standard.
Cookie:
I haven’t seen this cookie format elsewhere and I think it is exclusive to Empire. As we look at more traffic, we find that the value of the cookie is constantly changing. Its format and number of characters seem to have some valuable content in this tool. If you notice that the cookie content started with the word “session”, which is a unique value, then a 27-character value is inserted between the = marks.
This 27-character is part of the encryption key that this tool uses.
User Agent:
This part (User-Agent) can be easily changed by an attacker Even newcomers can easily change it.
HTTP Response analysis:
HTTP/1.0 200 OK :
That is, the response server supports the “HTTP 1.0” protocol standard, and the fields contained in the HTTP Response must comply with “ HTTP 1.0”.
Cache-Control and Pragma :
There is no “Cache-Control” field in the “HTTP 1.0” RFC. Cache-Control is for “HTTP 1.1” RFC. HTTP 1.0 uses the “pragma: no-cache” field to control the cache, but there is both a “Cache-Control” field and a “pragma: no-cache” field, indicating that this Response is suspicious.
Content-Length:
In the Empire tool in the HTTP module, the most important field in the HTTP Response is the Content-Length field.
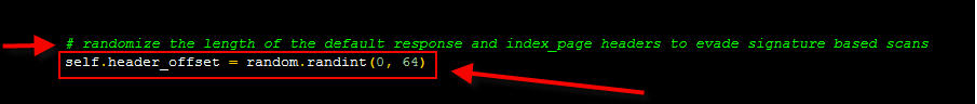
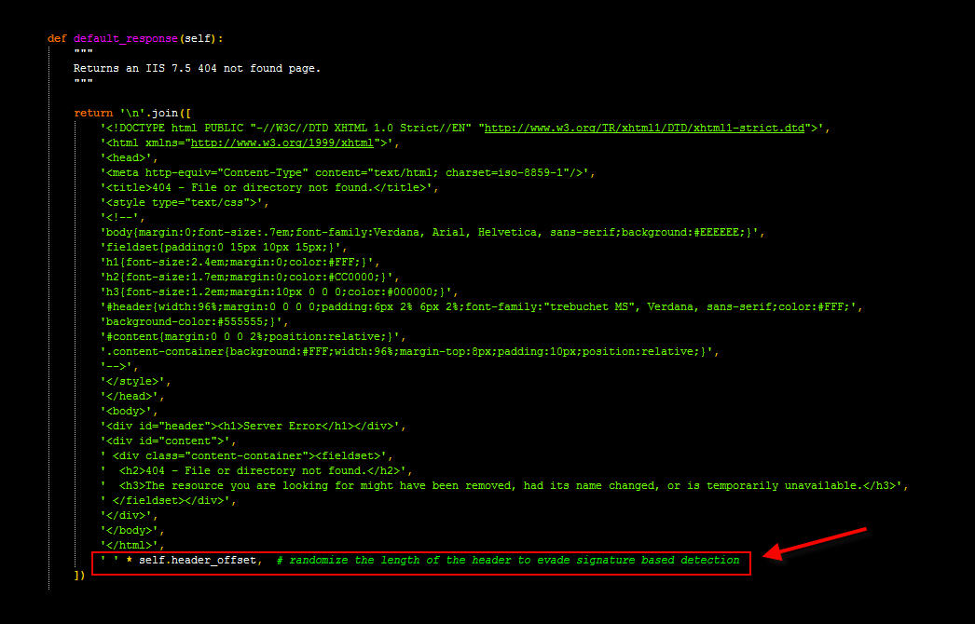
In the figure above, which is the output of the Wireshark tool, go to the last line after . In the above figures, there is some space after . As you can see, this tool randomly inserts a space at the end of the HTTP Response so that it is not detected by signature-based detection tools.
The constant value of Content-length in HTTP Response is 1213, which adds a random number from zero to 64, up to a maximum of 1277, which is the best item to detect.
Conclusion:
Consequently, to detect Empire HTTP traffic, from one source to a destination, You should see at least the following in HTTP traffic:
• Content-length value in HTTP Response should be between 1213 and 1277.
• The cookie value starts with a “session” and has 27 characters.
• Both the URI and User-Agent fields can be used to reduce the False Positive.